Unlock the Benefits of Identity Transformation
With Netdata’s Identity Transformation, you achieve:
We streamline identity management with secure, user-friendly authentication and adaptable processes for all users. With our expertise, you will be able to manage identities effectively, enhance user experiences, and reduce risks, ensuring robust protection for your business.
With Netdata’s Identity Transformation, you achieve:
We provide simplified, secure user authentication to improve customer and employee satisfaction.

We help you integrate rapid, seamless access processes that boost productivity and user interaction.
We minimize attack surfaces through advanced role-based access and robust identity governance
Identity management doesn't have to be a burden. Discover how Netdata's Identity Transformation solutions deliver secure, user-friendly access control that adapts to your business needs, enhances efficiency, and minimizes risk.

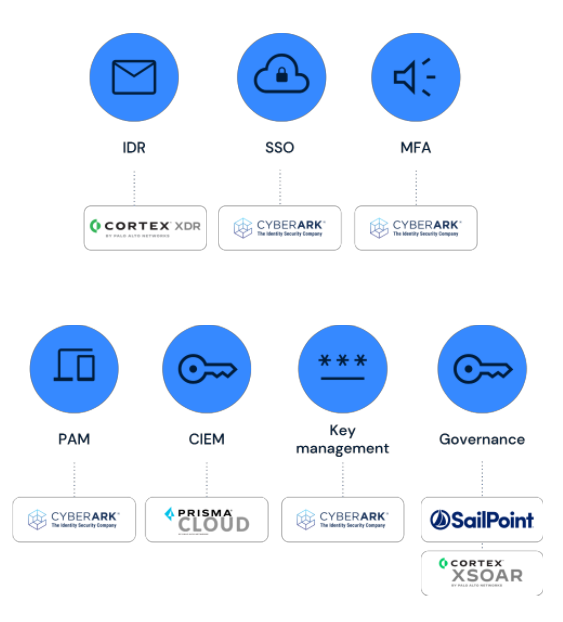
Our innovative solutions simplify identity management and safeguard your organization. Identity Transformation’s services include:
